Final Exam: GovNet
Out: Wednesday, 5 December 2000
Due: Monday, 10 December 2001 at 5:00 PM
Drop off at Dave's office no later than 5:00 PM on Monday. If I do not have your final then, I will be unable to grade it before the final grades are due.
Rules
Work alone. Do not talk to anyone about this final or content related to this course between receiving this exam and 5:00 Monday.
You may use any non-human resources you want. Remember to cite any outside resources you use. This is not meant to be a research project, you should be able to answer this question well based on what you already know from the class.
There is no time limit. But, it is unlikely to be helpful to spend inordinate amounts of time on this. I recommend reading the question right away and thinking about it, and not spending more than 5 hours on your responses.
You may turn in up to five pages total with writing only on the front of each page. If you turn in more than five pages, I will pseudorandomly select five of the pages you turn in to read. You should not use tricks like small font sizes or no margins to get around the spirit of the page limit. It is possible to answer these questions well using many fewer than five pages.
Background
GSA to Lead Effort for President's Cyberspace Security Advisor
Washington, DC -- At the request of the President's Cyberspace Security Advisor, the U.S. General Services Administration today released a Request for Information (RFI) to the U.S. telecommunications industry seeking information and suggestions for the development of a special telecommunications network.
A key feature of this network, called GOVNET, is that it must be able to perform its functions with no risk of penetration or disruption from users on other networks, such as the Internet. GOVNET is planned to be a private voice and data network based on the Internet Protocol (IP), but with no connectivity with commercial or public networks.
...
US General Services Administration, Press Release, 10 October 2001
ComputerWorld, 26 October 2001
Speaking here at a recent conference on data integration and national security sponsored by Fairfax, Va.-based WebMethods Inc., Woolsey said the concept of establishing a virtual private network called GovNet is "well and good," but fatally flawed. The idea has been put forth in recent weeks by Richard Clarke, President Bush's special adviser on cybersecurity (see story).
"The problem is that not absolutely everyone in the government is guaranteed to be on our side," said Woolsey. "Once you get into the network, you have pretty much free access. So you haven't really solved the problem."
Instead, said Woolsey, "You have created something in which there is a huge premium for Iraqi intelligence or Osama bin Laden to find some American who is willing to help him and be a clever hacker."
GovNet would be one of possibly a series of virtual private networks that could insulate critical national services, such as those provided by the Federal Aviation Administration and the finance industry, from hackers and distributed denial-of-service attacks. Private-sector recommendations on GovNet are due Nov. 21, and the government plans to post an analysis of the recommendations and a timeline for moving forward by the end of January.
Woolsey said the GovNet concept doesn't take into account the high level of sophistication of state-sponsored terrorists and hackers who are likely capable of breaking through most of today's perimeter network security protections. "Relying on a filter that tries to distinguish bad code from good code over the long run is a mug's game," said Woolsey. "The smarter the hacker, the easier it's going to be for him to make bad code look like good code."
...
Questions
Based on your stellar performance in CS588, you have been hired to as chief architect to design a secure network for government agencies known as GovNet.The best cryptography experts at the NSA have recommended the following primitives:
- AES, a symmetric cipher. AES can be used securely with a 128-bit key and 128-bit block size. AES is efficient.
- RSA, a public-key cipher. RSA can be used securely with 2048-bit primes. RSA is slow.
- SHA, a cryptographic hash function. SHA produces a 160-bit digest.
- Tiny, a cryptographic pseudo-random number generator.
Consider the simple GovNet:
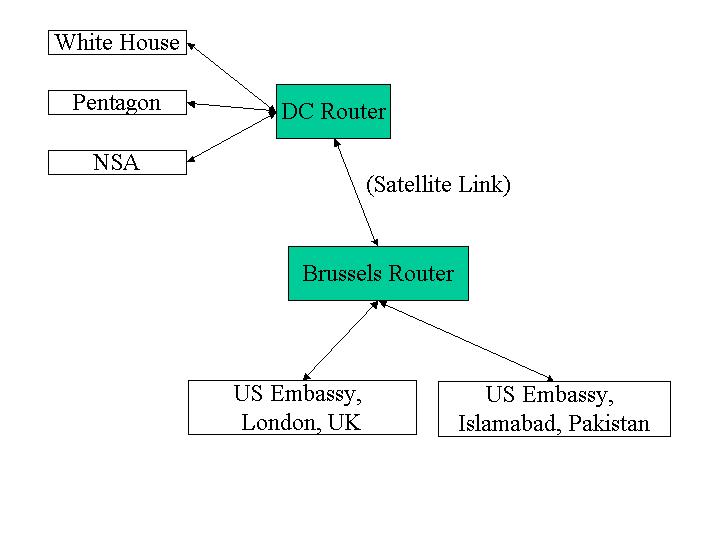
1. Router-Router Communication (25)
The NSA is worried about foreign governments tapping into the communication channels used by GovNet and recommends that all network transmissions be encrypted using AES (Rijndael). End users cannot be trusted to securely encrypt their transmissions, so encryption must be done by the routers before sending a message over a link.
Describe your design for sending messages between the DC and Brussels routers. It should explain clearly how a message is transmitted and received, how any keys are established and distributed, and any assumptions you make about performance and security tradeoffs. You may assume that the two routers are constructed in a secure facility in Langley, VA, and transported under close guard to secret locations in Washington, DC and Brussels, Belgium.
All satellite transmissions, of course, can be intercepted. The NSA reminds you that it would be unwise to transmit a large amount of data using the same key. The routers can store a few kilobytes of information.
Assume that the routers are kept in physically secure locations guarded by trustworthy soldiers, so there is no chance they could be compromised.
2. Joining the GovNet (25)
Agencies on the GovNet set up a gateway router that is connected over a land-line to one of the master routers. For example, the Pentagon sets up a gateway connected to the DC router. You may assume agencies join the GovNet infrequently, but need to do so with equipment they install locally. (That is, the gateway router that is installed at the Pentagon should not come preconfigured with any secrets stored on it, since it is vulnerable to tampering before it is installed in a secure location.)
Describe the process for an agency to set up a gateway router for the GovNet. Explain clearly how messages are transmitted between that gateway router and the master router. You should not assume the land-line connection between the two routers can be protected from passive or active eavesdropping.
3. Setting up Desktop Machines (25)
Once an agency has a gateway router, it should be able to set up local area network machines to be on the GovNet.
Penny Thrifty suggests that the GovNet machines in the Pentagon can use the same local area network as the normal machines (connected through a different gateway router to the Internet) in the Pentagon since the internal wiring in the Pentagon is very secure.
Design a scheme for setting up local GovNet machines and explain how they send and receive messages through the GovNet gateway. To be useful, it must be possible to have GovNet machines on desktops in offices that are somewhat insecure.
Explain any unreasonable risks associated with running the GovNet machines on the same local area network as the normal, Internet-connected machines. What restrictions would you place on how the local machines are used?
4. Should we build GovNet? (25)
Write an essay (no longer than 1 page) arguing for or against establishing a GovNet. Your essay should be substantially more techincal than either of the background articles above.
