Manifest: Monday 10 September 2001
| Assignments Due | |
| Today | Problem Set 1 |
| Monday, 1 October | Projects Preliminary Proposal |
SPEAKER: Carl E. Landwehr
Mitretek Systems, Inc.
TOPIC: Ten Unsolved Problems in Information Assurance
Some of the earliest electronic computers were built for reasons
of national security -- to decipher enemy messages, compute
trajectories, or develop weapons -- but security of programs and
data became a concern only when computers began to be shared
among users. The interconnection of computers, their increasing
ubiquity, and their use in critical systems expanded security
concerns and changed the focus of those concerns somewhat.
Research has now been conducted in this general area for over
three decades. Many problems have been identified, and some have
been solved, yet we still seem plagued with systems that are not
really trustworthy. After a brief historical introduction, this
talk will review a number of problems that still demand the
attention of scientists and engineers.
DATE: Friday, September 14, 2001
TIME: 3:30 p.m.
PLACE: Olsson 009
Refreshments will be served in the Lounge (Room 224) at 3:00 p.m.
- FIPS Data Encryption Standard - As there are over 70,000,000,000,000,000 (seventy quadrillion) possible keys of 56 bits, the feasibility of deriving a particular key in this way is extremely unlikely in typical threat environments.
- DES Key Search Project
- Electronic Frontier Foundation's DES Cracker Project
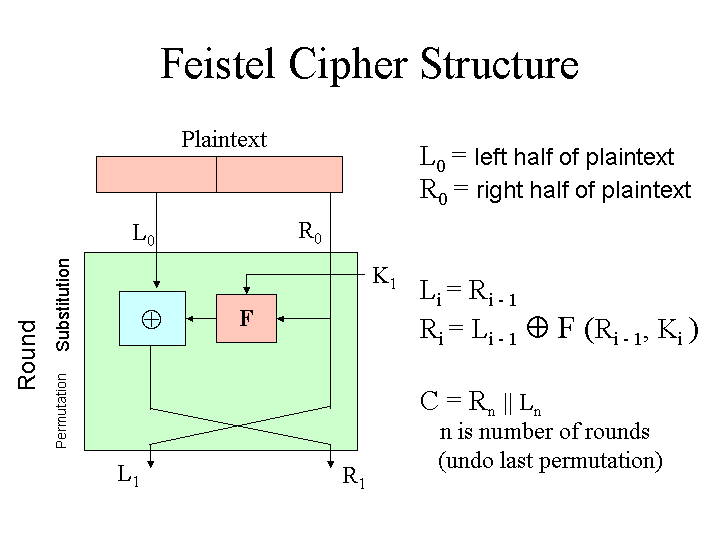
- What are the advantages and disadvantages of block ciphers?
- What are diffusion and confusion and what are they important?
- How does a Feistel cipher work?
- How secure is DES?
- What makes a DES key weak?
DEAR SIR -- A favorable and a confidential opportunity offering by Mr. Dupont de Nemours, who is revisiting his native country gives me an opportunity of sending you a cipher to be used between us, which will give you some trouble to understand, but, once understood, is the easiest to use, the most indecipherable, and varied by a new key with the greatest facility of any one I have ever known. I am in hopes the explanation inclosed will be sufficient. Let our key of letters be [some figures which are illegible] and the key of lines be [figures illegible] and lest we should happen to lose our key or be absent from it, it is so formed as to be kept in the memory and put upon paper at pleasure; being produced by writing our names and residences at full length, each of which containing 27 letters is divided into two parts of 9. letters each; and each of the 9. letters is then numbered according to the place it would hold if the 9. were arranged alphabetically, thus [so blotted as to be illegible]. The numbers over the letters being then arranged as the letters to which they belong stand in our names, we can always construct our key. But why a cipher between us, when official things go naturally to the Secretary of State, and things not political need no cipher. 1. matters of a public nature, and proper to go on our records, should go to the secretary of state. 2. matters of a public nature not proper to be placed on our records may still go to the secretary of state, headed by the word `private.' But 3. there may be matters merely personal to ourselves, and which require the cover of a cipher more than those of any other character. This last purpose and others which we cannot foresee may render it convenient and advantageous to have at hand a mask for whatever may need it. But writing by Mr. Dupont I need no cipher. I require from him to put this into your own and no other hand, let the delay occasioned by that be what it will.
From Thomas Jefferson's letter to the U.S. Minister to France (Robert R. Livingston), Washington, Apr. 18, 1802.
