| Problem Set 5: Quantum Crypto Coloring Book - Selected Answers |
1. Maury Bond's Coloring Crypto
This question is inspired by a question by Giuseppe Ateniese.
Maury Bond's secret agents (from Problem Set 1, question 6) never did manage to decode the message and locate the super ray gun. Last he heard, they were still in Borneo XOR'ing random bits.
Maury has decided to recruit three new secret agents: Abby Avaricous, Billy Badd and Carrie A. Grudge. This time, however, he will avoid the problems with revealing bits in order by encoding the mesesage on three transparencies such that they can be placed on top of each other to reveal the message all at once. Any two transparencies by themselves should reveal no information, but when the three are aligned correctly on top of each other, everyone will see the message appear at the same time.
a. (30) Explain how Maury can create the three transparencies. You may find it useful to use an encoding scheme based on the primary subtractive colors - cyan (C), magenta (M) and yellow (Y). Cyan absorbs red; magenta absorbs green; and yellow absorbs blue. The following relations hold when transparencies of these colors are placed on top of each other:
Yellow + Cyan = Green
Yellow + Magenta = Red
Cyan + Magenta = Blue
Cyan + Magenta + Yellow = Black
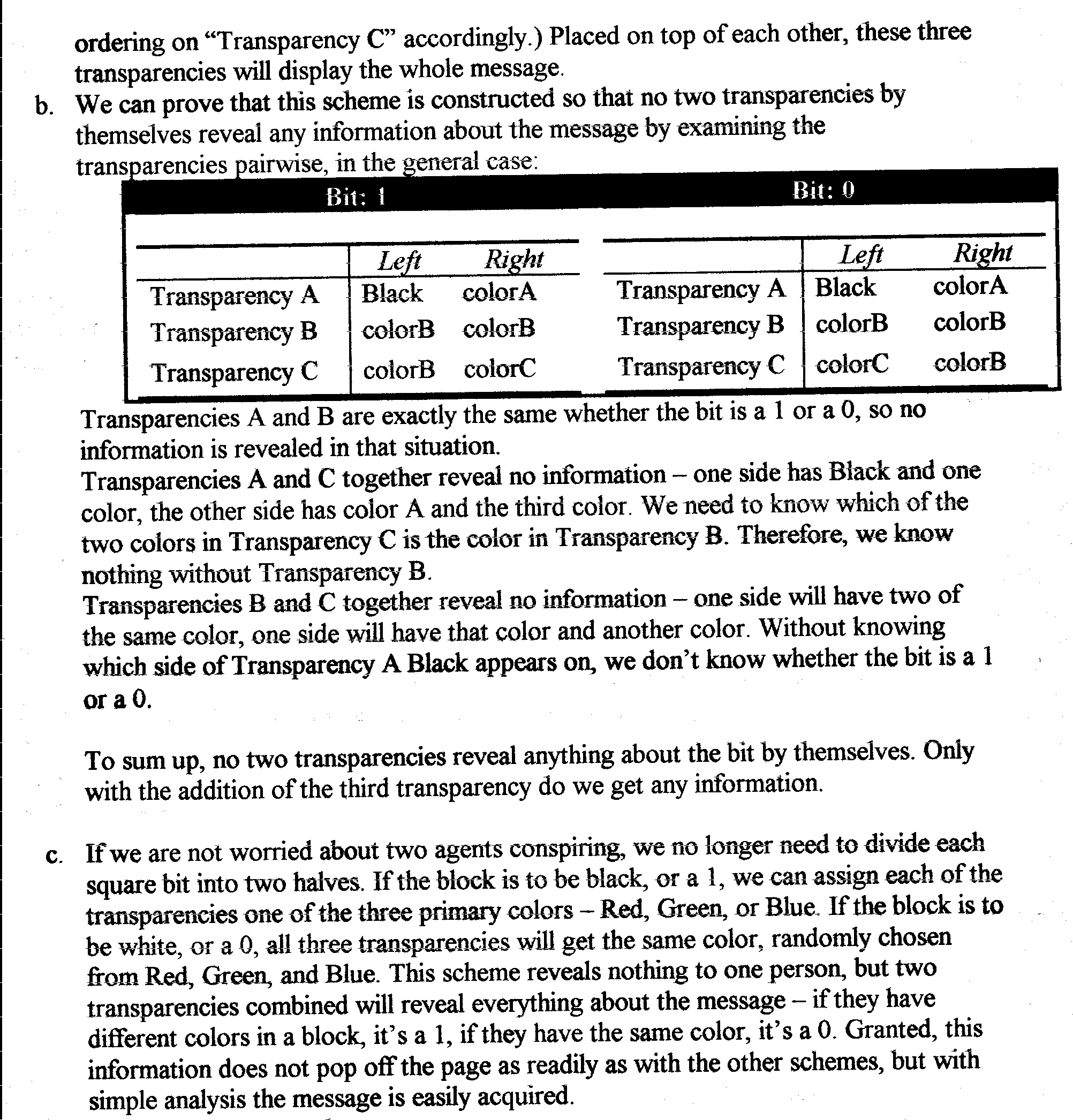
b. (15) Prove that your scheme is perfectly secure in an information-theoretic sense. That is, no two transparencies by themselves reveal anything interesting about the message.
c. (15) Maury fears that one of the three agents may be killed. He decides he is no longer worried about two agents conspiring. Instead, he would like to make sure that any two agents can combine their transparencies to reveal the message, but each agent by herself has no information. Describe a scheme that satisfies this requirement.
d. (up to 50 bonus points) Implement your scheme from either part a or c to produce transparencies encoding a message that demonstrate your scheme works.
Answer:
Several students found Moni Naor and Adi Shamir's Visual Cryptography paper (there was a link to this on the 7 Nov manifest) which provides a solution to this problem that uses only black and white. The image is divided into horizontal, vertical and diagonal shares so that any two shares convey no information, and the third share can make the resulting square either black or dark grey (3/4 black). The fully black squares make up the image.
A better solution would take advantage of the colors to make the image appear more clearly. See Stephen Liang's answer:

Continued on next page
Comments: Several students submitted transparencies that clearly revealed something about the message with just two (or even a single transparency), but still submitted proofs claiming their scheme was perfect. I graded these much more harshly than people who acknowledged that their scheme was imperfect, instead of constructing a bogus proof, since it is a lot more dangerous to claim something is secure that is not. Another issue with all of the implementations submitted, is the careless use of non-cryptographic pseudorandom number generators. Recall that most programming languages and operating systems do not provide cryptographically secure pseudorandom number generators, and if your implementation is highly vulnerable to attack if you use poor pseudorandom number generators.
Selected Transparencies and Code:
Jon Erdman, Eric Hutchins and Stephen Liang - an Excel spreadsheet with VBA macros that encode a Jefferson image on three colorful transparencies. (You need to enable Excel macros to try this. Click on "Generate Transparencies".)
Mike Hogye used a scheme based on Moni Naor and Adi Shamir's to produce these transparencies:
- Abby's Horizontal
- Billy's Diagonal
- Carrie's Vertical
- Horizontal + Vertical
- Horizontal + Diagonal
- Vertical + Diagonal
- All Three
Michael Neve and Eric Peeters:
Adam Sowers:
- zip file containing MS C++ project files and source code, and image bitmaps
- C++ Source Code
- Original Image
- Blue Share
- Green Share
- Red Share
2. Quantum Leap
Bennet's Quantum Key Distribution scheme from Lecture 16 allows Alice and Bob to establish a shared secret key with perfect secrecy with on average 2 photons transmitted per bit (i.e., for each photon transmitted, there is a 50% chance Alice and Bob will agree on a key bit).Alice, Bob and Coleen would now like to establish a common secret key (all three of them will know the same key, but no one else can know anything).
(40) Describe a quantum key distribution scheme three people can use to establish a secret key. For full credit, your distribution scheme should require less than 4 photons transmitted per bit, and must be perfectly secure against all forms of both passive and active eavesdropping.
Answer:
This question is a lot harder than it seems. My hint about requiring less than 4 photons transmitted per bit was intended to get you thinking about what is wrong with the obvious answer of just having Alice transmit the same sequence of photons to both Bob and Coleen and then having them determine which ones they both guessed the correct filters to agree on the key, and do a validation test to confirm that there was no eavesdropping. Since each would have a 50% chance of guessing correctly, the probability that both guess correctly is 25% and they would establish a 3-way shared key with an average of 4 photons transmitted per key bit.
There is a serious problem with this scheme however! (Only Keen Browne noticed it.) If Alice transmits the same exact photon sequence to Bob and Coleen as separate streams, is it as secure from eavesdropping as if she only transmits it once?
Recall the original 2-party quantum key distribution protocol. Suppose Alice transmits a photon h to Bob. Eve intercepts the photon. Suppose without loass of generality that Eve uses the rectilinear detector. If Alice used the rectilinear encoding (50% probability), Eve would receive the correct photon. But, Eve doesn't know which encoding Alice used, so there is a 50% probability she is wrong. Suppose without loss of generality that she detects a V photon. Then Eve knows there is a 50% probability h was a V photon, and 25% probability it was a +45 degree photon, and 25% probability it was a -45 degree photon. We argued for Bennet's scheme that this was good enough, since if Eve sends a photon towards Bob, there is a 50% chance she will guess the wrong photon, and 50% chance Bob will guess the correct filter for this photon, and if he guesses the correct filter there is a 50% chance Eve's photon will get through correctly. Hence, with the original 2-party key distribution, for each bit Eve intercepts, there is a .5 * .5 * .5 = .125 probability Bob would get the wrong bit. (How likely this makes it for the interception to be detected depends on how Alice and Bob confirm that Bob received the correct key, but let's assume that it can be nearly 100% without sacrificing much security using a good hashing function.)
But what if Alice transmits identical photons to Bob and Coleen, and Eve intercepts both of them? Certainly, Eve can use this information to improve her chances of guessing the right photon spin and retransmitting the identical photons without getting caught. Continuing the example above, suppose Eve uses a V filter on the identical photon Alice sent to Coleen. If the transmitted photon was a V photon, it will go through the filter 100% of the time. If it was an -45 or +45 photon, it will go through the filter 50% of the time. So, compared to the 2-party protocol, now 50% of the time if the photon was -45 or +45, Eve will know it is not a V photon. Hence, she will have 50% probability of guessing either -45 or +45 correctly. This improves the probability she will guess the photon correctly to .75, and the probability she can detect one bit without getting caught to .25 * .5 * .5 = 0.0625. (There may be better choice for the two filters Eve uses to improve this further, although with only two identical photons she cannot get the correct spin all the time. It is left as an exercise to the reader to determine better choices for the filters, and how high the probability Eve could get away with eavesdropping would be if Alice, Bob, Coleen and Doug attempted to use a straightforward 4-party key distribution scheme.)
