 |
|
 |
|
 |
|
 |
|
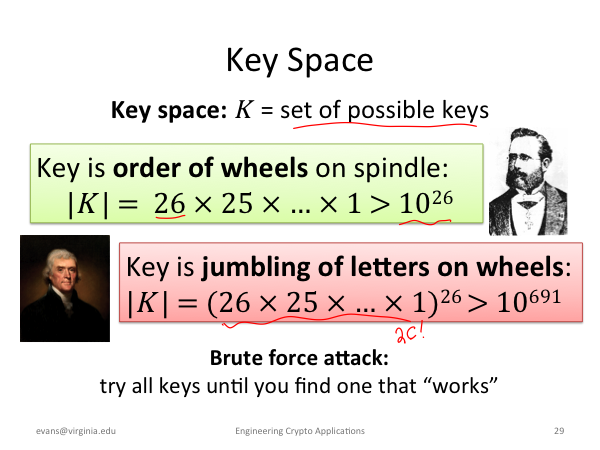 |
There are, of course, better ways to break a message encrypted using Jefferson's Wheel cipher than just trying all possible keys as in a brute force attack. Here's how Geoff Stoker solved it: Jefferson Wheel Challenge solved!. |
 |
|
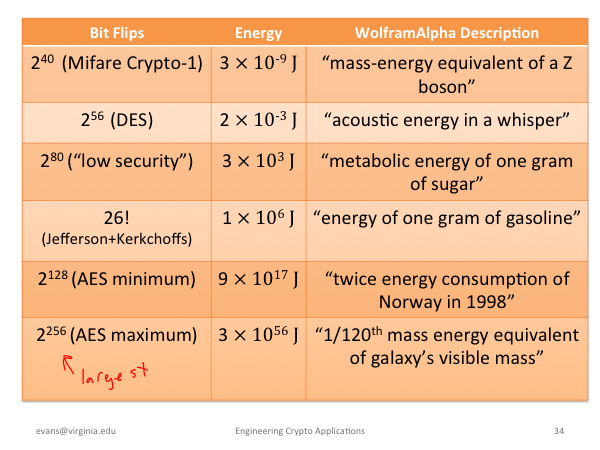 |
Wolfram Alpha Search |
 |
|
 |
|
 |
|
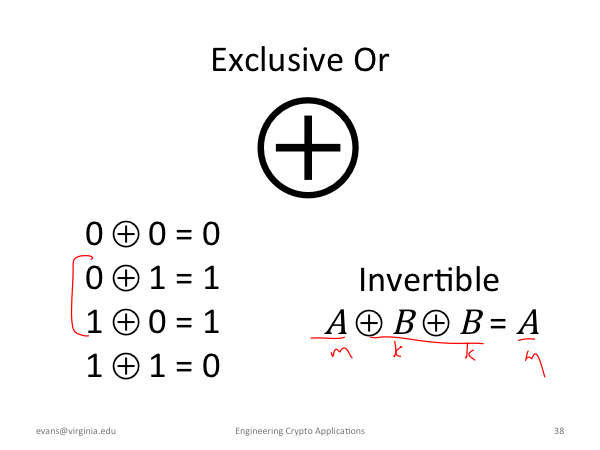 |
|
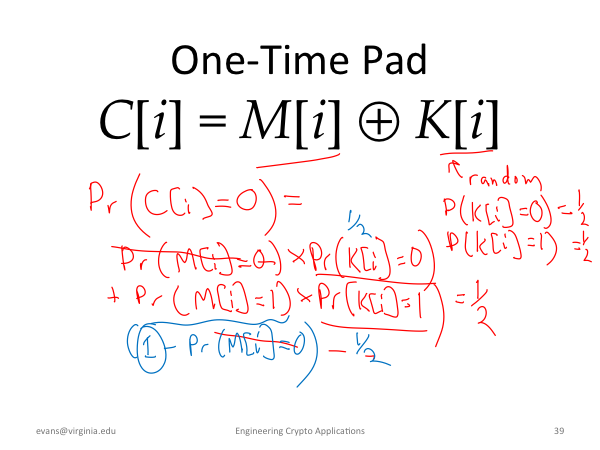 |
|
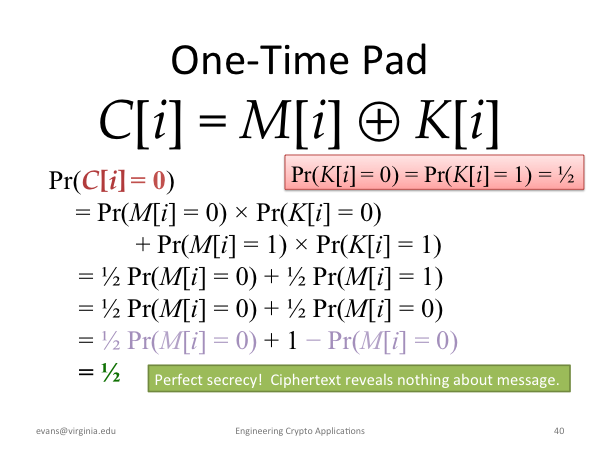 |
|
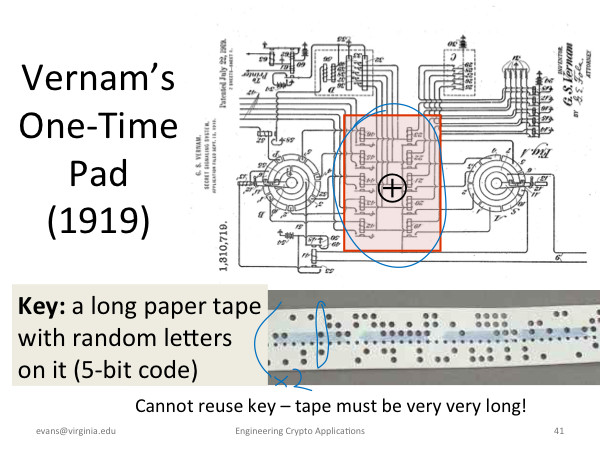 |
|
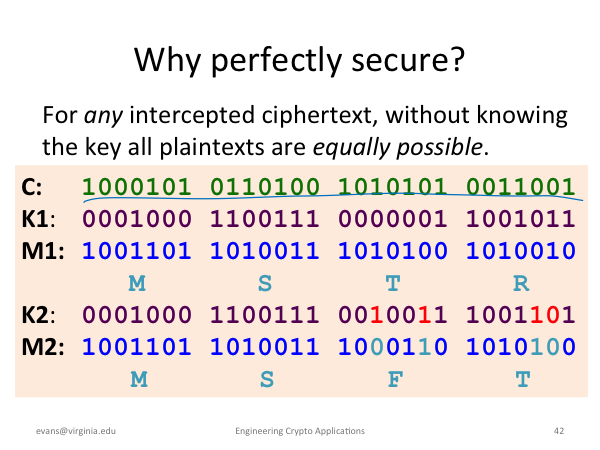 |
|
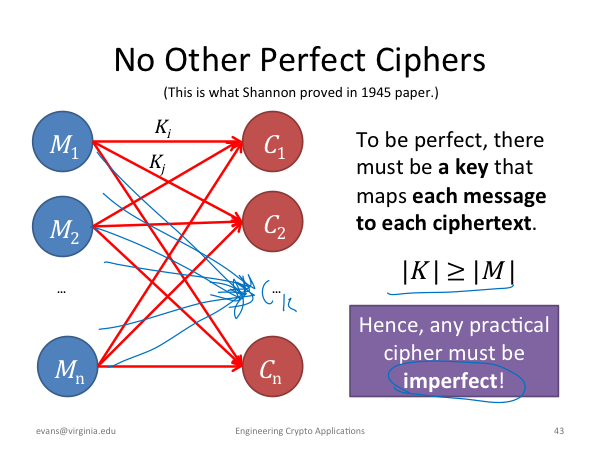 |