Final Exam: GovNet - Comments
General Comments
Building GovNet is obviously a huge project, well beyond the scope of what would be reasonable for a final exam question. On the other hand, most of the specific questions you were asked could be addressed fairly simply. Good answers revealed clear understanding of key concepts from the course, and most students were able to do that.
Keep it Simple. Simple answers are almost always better than complex ones. Complicated solutions tended to either have fatal flaws or be so incomprehensible I couldn't figure out what they had in mind. The way to present a complex answer is to present a simple one first, and then explain why the complexity was added.
Shorter is better. There was a reason for the five page submission limit, and a few people disregarded this. The bad reason, of course, is to save me from having to read really long answers. The good reason, is that a strict page limit does force you to think more about how to present your answer and to edit your writing to emphasize the most important points and avoid unnecessary repetition. In general, shorter answers were better. (Except on the last essay question, where it was hard to get a good grade with a very short essay that didn't consider things deeply enough.)
Don't reinvent your own crypto to solve known problems. Many students developed new protocols that attempted to do what known protocols already do. For example, if SSL does what you need, use it! Inventing your own protocol is risky, and often error-prone. Even if your new protocol doesn't have any obvious flaws, it has not been evaluated so you would need a careful analysis to convince someone it is secure. Anytime you invent a new protocol, you need to explain clearly why it is necessary - what is it about obvious known alternatives that don't satisfy the requirements.
Avoiding sexist language is hard. I was pleased I didn't have to penalize any groups for sexist language in your reports, but several of you reverted to your normal dialect for the final (which there was no penalty for). Others made heroic efforts to avoid sexist language - this is good, but of course, if it is clear to the reader that you are making such heroic (heroine-ic?) efforts then the prose is probably not flowing as smoothly as it should. Present-day English makes it really hard to write without revealing the sexist traditions of the language; this takes practice, but is important.
Questions
Based on your stellar performance in CS588, you have been hired to as chief architect to design a secure network for government agencies known as GovNet.The best cryptography experts at the NSA have recommended the following primitives:
- AES, a symmetric cipher. AES can be used securely with a 128-bit key and 128-bit block size. AES is efficient.
- RSA, a public-key cipher. RSA can be used securely with 2048-bit primes. RSA is slow.
- SHA, a cryptographic hash function. SHA produces a 160-bit digest.
- Tiny, a cryptographic pseudo-random number generator.
Consider the simple GovNet:
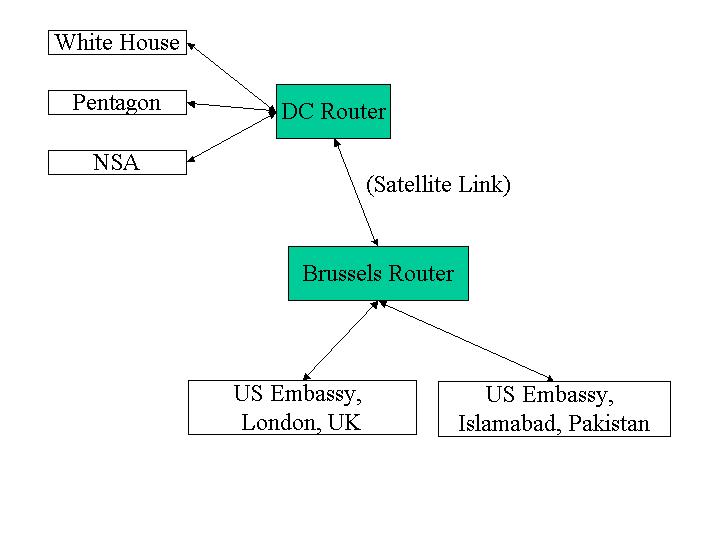
1. Router-Router Communication (25)
The NSA is worried about foreign governments tapping into the communication channels used by GovNet and recommends that all network transmissions be encrypted using AES (Rijndael). End users cannot be trusted to securely encrypt their transmissions, so encryption must be done by the routers before sending a message over a link.
Describe your design for sending messages between the DC and Brussels routers. It should explain clearly how a message is transmitted and received, how any keys are established and distributed, and any assumptions you make about performance and security tradeoffs. You may assume that the two routers are constructed in a secure facility in Langley, VA, and transported under close guard to secret locations in Washington, DC and Brussels, Belgium.
All satellite transmissions, of course, can be intercepted. The NSA reminds you that it would be unwise to transmit a large amount of data using the same key. The routers can store a few kilobytes of information.
Assume that the routers are kept in physically secure locations guarded by trustworthy soldiers, so there is no chance they could be compromised.
Comments:
Because the routers were constructed in a secure facility, there is an opportunity to put secrets on them before they are deployed. This avoids the traditional key distribution problem.
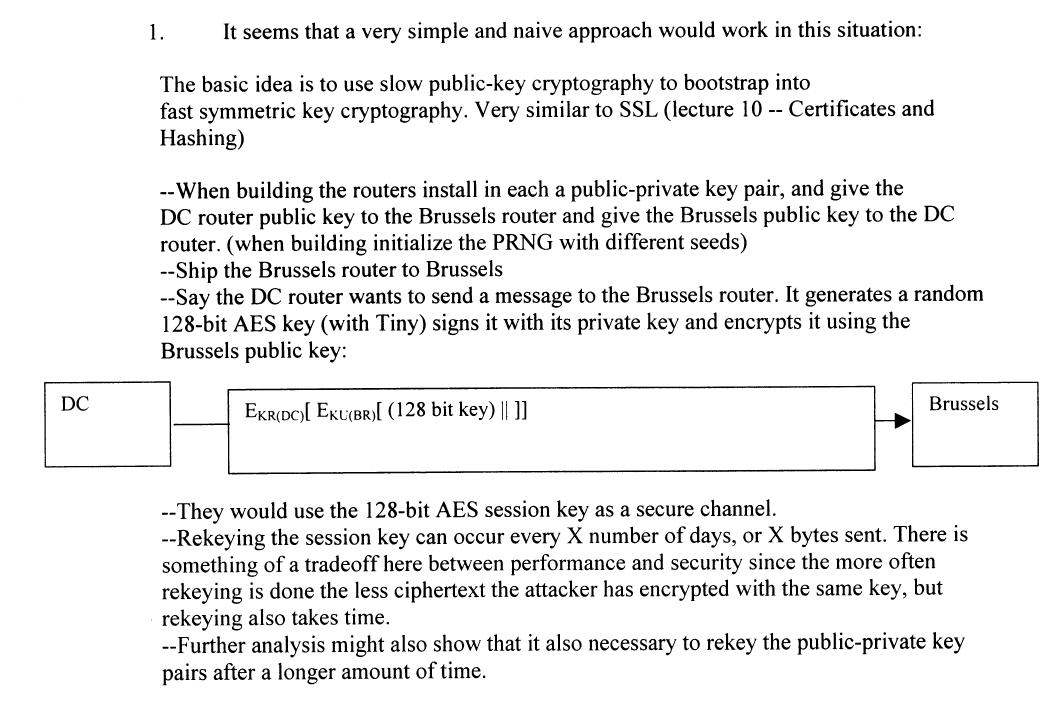
The simplest approach is to use an RSA key pair to distribute new AES keys to use for transmissions. Instead of calling the keys public and private, we will call them "d-key" and "e-key" (we want to avoid confusion with calling one of the keys public, since in fact both will be kept secret). We take advantage of these properties of RSA: D (E (M)) = M and E (D (M)) = M.
We can generate the initial key pair by seeding Tiny with a true random source, such as measuring radioactive decay. The d-key is installed on the DC router, and the e-key on the Brussels router. The keys are stored on the routers using write-once memory (that is, they cannot be changed once installed). Security depends on both these keys being kept secret.
The RSA keys are used to send AES keys for message transmission. Because of the computation required to do RSA, we want to use the much faster AES cipher for all other messages. The DC router can establish a new AES key by generating a new 128-bit key k using Tiny, and sending D (k) to the Brussels router, which can obtain k using E. Symmetrically, the Brussels router can establish a new AES key by sending E (k) to DC. These key change messages can be proceeded by a AES-encrypted (using the old key) special key change packet.
The frequency of key changes is a tough question. Most of you proposed excessively frequent key changes. The time of the key changes should be unpredictable (no sense making it easy for an attacker to know when the key changes) and should depend on both the amount of data sent (more data with the same key helps the cryptanalyst, but realistically for AES even terabytes don't help significantly with any known attack) and the time (since if a key is compromised, you want to limit the amount of damage that is done).
Security of the key messages depends on RSA, but it is even better that normal since the public key is not know to the attacker. This means, the attacker does not know n, so cannot even being a factoring attack.
A few people suggested using undersea cables as a secure alternative to satellites. They are probably a bit harder to jam (prevent any message transmission), but certainly not impossible. I recommend Blind Man's Bluff by Sherry Sontag and Christopher Drew for some amazing stories of how US submariners were able to tap Soviet undersea cables during the Cold War.
Here are two full-credit answers:
2. Joining the GovNet (25)
Agencies on the GovNet set up a gateway router that is connected over a land-line to one of the master routers. For example, the Pentagon sets up a gateway connected to the DC router. You may assume agencies join the GovNet infrequently, but need to do so with equipment they install locally. (That is, the gateway router that is installed at the Pentagon should not come preconfigured with any secrets stored on it, since it is vulnerable to tampering before it is installed in a secure location.)
Describe the process for an agency to set up a gateway router for the GovNet. Explain clearly how messages are transmitted between that gateway router and the master router. You should not assume the land-line connection between the two routers can be protected from passive or active eavesdropping.
Comments:
The key difference from question one is that there is no way to preconfigure the gateway router with secrets.
Several different approaches were suggested for dealing with this. One approach is for the master router to generate a new RSA key pair, store the E-key in write-once memory, and write the D-key on a write-once storage card. This card is carried by a trusted courier to the gateway location. The gateway router has a one-use interface for reading a key from a card. This interface is designed physically so it can only be used once, and tampering would be noticable (for example, the slot is covered by a hologram). The courier inserts the key card, which is sealed in a tamperproof way into the gateway router.
To communicate, the master router generates a new AES key and sends E(k) to the gateway. The gateway obtains k using D. This is preferable to the gateway generating the shared key, since we only need to put true random entropy generation on the master router.
Other approaches used hash chains. This is pretty risky in this application - if one of the keys is broken, the attacker can determine all subsequent (or all prior, depending on how you did the hashing) keys.
3. Setting up Desktop Machines (25)
Once an agency has a gateway router, it should be able to set up local area network machines to be on the GovNet.
Penny Thrifty suggests that the GovNet machines in the Pentagon can use the same local area network as the normal machines (connected through a different gateway router to the Internet) in the Pentagon since the internal wiring in the Pentagon is very secure.
Design a scheme for setting up local GovNet machines and explain how they send and receive messages through the GovNet gateway. To be useful, it must be possible to have GovNet machines on desktops in offices that are somewhat insecure.
Explain any unreasonable risks associated with running the GovNet machines on the same local area network as the normal, Internet-connected machines. What restrictions would you place on how the local machines are used?
Comments: Unlike routers, the desktop machines are likely to be associated directly with people. Hence, we install the machines on the network but our real concern is authorizing and authenticating the people. Someone needs to decide who should gain access to the GovNet. This will probably involve administrators who make decisions and a background check process similar to what the NSA does before hiring someone. (Naturally, the severity of the process limits who can benefit from GovNet.)
Once someone has been granted access, the gateway router generates an RSA key pair for them. The E-key is stored on the gateway router, and the D-key is stored on a card given to the authorized individual encrypted with a password selected by the individual (and checked for security by a password cracking application). In addition, usage access may be stored into the gateway router (for example, what other sites this individual may communicate with, times when she may communicate, limits on network usage, etc.).
The GovNet desktop machines contain card readers. To log in, the user swipes her card through the card reader. This reads the card ID, and transmits it to the gateway. The gateway generates a random number r and a random AES key k, and sends E (r || k) to the desktop. The user then enters her password into the card reader, which uses this to obtain D and calculates r and k by decrypting E (r). The reader sends back r (plaintext is fine) to the gateway, and uses k as a symmetric AES key for this session. The session will time out after 30 minutes or if the user is idle for more than 1 minute, requiring the login process to be repeated. This way if a user forgets to log out before leaving the office, the risks the connection will be compromised are minimal.
The gateway router can check packets sent out by the user have a valid packet header, and conform to the access controls for that user.
Sharing a LAN with normal Internet machines is pretty risky. Assuming the encryption works, interception is not likely to be a big problem. The risk of denial-of-service attacks flooding the LAN, however, is real. A firewall on the normal Internet gateway that prevents attacks from reaching the LAN can help, as well as a strict policy against mobile code (e.g., no reading email with Outlook).
4. Should we build GovNet? (25)
Write an essay (no longer than 1 page) arguing for or against establishing a GovNet. Your essay should be substantially more techincal than either of the background articles above.
Comments:
The class was nearly evenly divided for and against GovNet (16 for, 18 against). The best answers included a discussion of who would use GovNet for what.
My personal view (which I tried not to let effect my grading on this, and think I didn't) is that GovNet makes sense only as an economic stimulus project.
Its pretty unclear what it would really be used for. We already have private networks for most essential services (military, banking, air traffic), and it seems a step backwards to try and unify them in one network. It doesn't make sense to make a GovNet that would be used for both highly sensitive and urgent communications, and routine government communications. The most sensitive communications aren't sent over a network, by using secure point-to-point lines or couriers. Whether or not there is a GovNet, the President's daily security briefing will be carried to him by hand, and the Pentagon will want its own secure link to the White House, not shared by the FAA or the IRS. For less essential communications, it is not clear why a GovNet would be better than using encryption on the public Internet or telephone networks. These networks have been remarkably reliable in practice, and I know of no instance when both the Internet and telephone networks were down for a significant time.
The security advantages a GovNet could offer are inversely related to its usefulness. If users were not allowed to access the Internet, use normal commercial software, install new programs, etc., it could be more secure against denial-of-service attacks than the Internet. On the other hand, it is unlikely many users would be able to give up those things.
The other significant risk with a GovNet is it provides attackers with a glamourous target. Centralizing government communications on one network makes it easy for a potential attacker to identify those communications. With a public network, government agencies who want to communicate securely can hide their communications in all the other Internet traffic (for example, by using Onion routing).
The technology issues of building a secure network are pretty well understood, and it seems likely that AES will be very secure for a long time and as explored in the other questions, we can distribute AES keys with good security. The people issues, though, are really hard. It seems inconceivable to me that our government could construct a GovNet without issues like who should control access to it being decided more by political issues than technical ones (remember the colonel with the really big safe in Feynman's "Safecracker Meets Safecracker"?). The military can (and does) run secure networks, but can do things a lot differently than civilian government. We should also remember that even high-ranking officials will do dumb things, and any system needs to be designed to make that as hard as possible (for example, see this report on what John Deutch was doing with his computer when he was director of the CIA).
See GovNet Proposal Sparks Plenty of Ideas, Debate, Washington Technology, 10 Dec 2001 for some more opinions.

