Sneakers
Note that the physical access you will have to my house at the movie night will have limited usefullness in the breaking into the grades file challenge. The machine that stores the file will be protected using a non-electrocuting version of the ideal firewall technique described in Lecture 20 during your visit (although my wireless network will be operating normally).
Final Preparation
- An opportunity to demonstrate good understanding of hash chains and cryptographic hashing.
- An opportunity to demonstrate good understanding of the mathematics behind RSA.
- An opportunity to demonstrate your ability to design and analyze protocols using public key cryptography
- An opportunity to demonstrate your facility in applying security principles to real world problems like voting.
2001 Problem Set 3
1. Key Distribution
a. (5) Suppose a council of n people want to establish keys so that any person may communicate secretly with any other person (that is each pair of people have a unique key). How many unique keys are necessary?Consider the following scheme for establishing 4-person secret communication:
Alice generate three secret keys, K1, K2 and K3 and securely gives Bob K2 and K3, Colleen K1 and K3 and Doug K1 and K2. Bob generates secret key K4 and gives it to Colleen and Doug. Hence, after meeting securely and distributing the keys each person knows the following keys:
A: K1, K2, K3Alice claims they can now all communicate securely with any other person since any pair of people know a pair of keys that no other pair of people know. Hence, if Alice wants to communicate with Bob, the will use KAB = K2 XOR K3. She claims this is secure since know one else knows both K2 and K3.
B: K2, K3, K4
C: K1, K3, K4
D: K1, K2, K4
Likewise,
KBC = 3 XOR 4b. (10) This scheme requires less total keys than the unique key per communicating pair scheme from part a. (Your answer to part a should confirm this.) Is any security sacrificed for the reduction in number of keys? (One way to answer this would be to describe trust models under which it is secure and insecure.)
KCD = 1 XOR 4
KAC = 1 XOR 3
KAD = 1 XOR 2
KBD = 2 XOR 4
c. (10) Can this scheme be scaled to allow 5 people to communicate with the same level of security as in (b), with 5 keys? (Explain how, or why not.)
2. Prime Directive
[Question due to Wade Trappe and Lawrence Washington]a. (5) Alice wants to securely send m to Bob. She selects p, a prime > m and integer a relatively prime to p - 1. She sends c = ma mod p and p to Bob over an insecure channel. Bob selects an integer b that is relatively prime to p - 1, computes d = cb mod p and sends d to Alice. Alice finds g such that ag ≡ 1 mod p - 1. (Recall since a is relatively prime to p - 1, it must have a multiplicative inverse mod p - 1.) She then computes e = dg mod p and sends e to Bob. Explain what Bob must do to obtain m.
b. (5) How vulnerable is this protocol to a passive eavesdropper?
c. (5) How vulnerable is it to an active eavesdropper?
3. Primal Tendancies
In the RSA paper, the authors claim that it is okay to use a probablistic prime number test since if a composite number is choosen the receiver would probably detecte it by noticing that decryption didn't work correctly.
That is, choosing a composite number is not likely to lead to a substantial security flaw, since the problem would be detected in the first transmission. Note that if it were not detected, choosing a composite number for p or
q would be bad, because an attacker would have an easier time factoring n = p * q = (p1 * p2) * q since one of the p factors is small (around sqrt (sqrt (n))).a. (10) Illustrate that decryption doesn't work if the choosen p is composite using an example. That is, pick p, q, e and d consistent with the RSA algorithm except p is composite, and show for some M: D (E (M)) ¹ M.
b. (5) Show how the proof that D (E (M)) = M breaks if p is composite. (You don't need to reproduce a complete proof, just identify the step of the proof that depends on p being prime.)
4. Annonymous Tallying
A group of students are trying to figure out how many of them read the RSA paper before class, but no one wants to reveal to anyone else whether or not they read the paper.We attempted (unsuccessfully) to do this in class by having the first student pick a random number to initialize the process. Then every student (including the first) adds one to the last number if she read the paper, and whispers it to the student next to her. The difference between the number at the end and the initialization number gives the total number of students who had read the paper.
Unlike our attempt to do this in class, the individuals are not able to communicate over a secure channel (e.g., whisper something to the person sitting next to them without others overhearing).
a. (10) Describe a protocol that can be used to annonymously tally the number of students who have read the paper without revealing anything about whether or not a particular individual has read the paper and without depending on any secure channels.
b. (5 + possible bonus) With the protocol we used in class, the first person can cheat and make the total any number she wants by revealing a different starting number. Any other person can cheat by modifying the passed number in some way other than adding zero or one (for example, someone could add 17 if he believes the class will be punished if the total is too low). Improve your protocol to make it resistant to these forms of cheating. (Of course, we can't do anything about individuals lying about whether of not they read the paper.)
5. Public-Key Poker
Alice, Bob and Cathy Sharky want to play poker. After seeing Cathy's shuffling skills, they decide it would be better to play on the Internet using virtual cards, then to use physical cards.A playing card deck has 52 cards. They agree to identify each card using a number:
suit = 0 | 1 | 2 | 3 (hearts, clubs, diamonds, spades) number = 1 (Ace) | 2 | 3 | ... | 10 | 11 | 12 | 13 cardid = (13 * suit) + numberso the queen of diamonds is card 26 + 12 = 38.
Play proceeds as follows:
- Alice, Bob and Cathy each generate RSA public-private key pairs: KUA (Alice's public key), KRA (Alice's private key); KUB, KRB; KUC, KRC. The public keys KUA, KUB, KUC are securely published.
- Alice generates a "deck" of 52 cards by encrypting the card identifiers (1-52) with KUA. She sends all the cards in random order to Bob.
- Bob encrypts all cards with KUB, and sends the cards in random order to Cathy.
- Cathy encrypts all the cards with KUC, and sends the cards in random order to Alice. At this point, the card m is encrypted as EKUC [EKUB [EKUA [m]]]].
- Alice chooses two cards, and sends the remaning 50 cards to Bob (and keeps a copy of them for herself).
- Bob chooses two cards from the cards Alice sent, and sends the remaning 48 cards to Cathy (and keeps a copy of them for himself).
- Cathy chooses two cards from the cards Bob sent, and sends the remaining 46 cards to Alice.
- Each player publishes their private keys. The all decrypt their cards and reveal their hands. Each player also decrypts the cards they passed to the next player to make sure no one cheated.
a. (8) Alice and Bob are subject to the UVA Honor Code, but Cathy has no such scruples. After Cathy gets royal flushes (the best poker hand) for the first few hands, Alice and Bob begin to get suspicious that Cathy might be cheating. How is it possible for Cathy to always pick the best cards (even though the private keys are kept secret and she can't break RSA)?
b. (5) Suggest a simple modification to the protocol that makes it (nearly) impossible for Cathy (or anyone else) to cheat.
c. (7) In a real poker game (for example "Texas Hold 'Em"), we need to deal hidden cards to each player but also deal some cards that are revealed to everyone. Consider a game where each player is dealt two secret cards, and then five community cards are dealt and revealed to everyone. We need to reveal the community cards to every player without revealing anything about the private cards until the end of the game. Modify the protocal so that after each player has their two hidden cards, the five community cards can be revealed.
6. Hashing
(10) Holly Hashly suggests creating a 128-bit hash of an arbitrarily long message by selecting a 128-bit prime number n, and a random 128-bit exponent e that is relatively prime to n and using Me mod n as a cryptographic hash function. Both e and n are public.How well does this satisfy the 5 properties of cryptographic hash functions?
2001 Final
Background
GSA to Lead Effort for President's Cyberspace Security Advisor
Washington, DC -- At the request of the President's Cyberspace Security Advisor, the U.S. General Services Administration today released a Request for Information (RFI) to the U.S. telecommunications industry seeking information and suggestions for the development of a special telecommunications network.
A key feature of this network, called GOVNET, is that it must be able to perform its functions with no risk of penetration or disruption from users on other networks, such as the Internet. GOVNET is planned to be a private voice and data network based on the Internet Protocol (IP), but with no connectivity with commercial or public networks.
...
US General Services Administration, Press Release, 10 October 2001
ComputerWorld, 26 October 2001
Speaking here at a recent conference on data integration and national security sponsored by Fairfax, Va.-based WebMethods Inc., Woolsey said the concept of establishing a virtual private network called GovNet is "well and good," but fatally flawed. The idea has been put forth in recent weeks by Richard Clarke, President Bush's special adviser on cybersecurity (see story).
"The problem is that not absolutely everyone in the government is guaranteed to be on our side," said Woolsey. "Once you get into the network, you have pretty much free access. So you haven't really solved the problem."
Instead, said Woolsey, "You have created something in which there is a huge premium for Iraqi intelligence or Osama bin Laden to find some American who is willing to help him and be a clever hacker."
GovNet would be one of possibly a series of virtual private networks that could insulate critical national services, such as those provided by the Federal Aviation Administration and the finance industry, from hackers and distributed denial-of-service attacks. Private-sector recommendations on GovNet are due Nov. 21, and the government plans to post an analysis of the recommendations and a timeline for moving forward by the end of January.
Woolsey said the GovNet concept doesn't take into account the high level of sophistication of state-sponsored terrorists and hackers who are likely capable of breaking through most of today's perimeter network security protections. "Relying on a filter that tries to distinguish bad code from good code over the long run is a mug's game," said Woolsey. "The smarter the hacker, the easier it's going to be for him to make bad code look like good code."
...
Questions
Based on your stellar performance in CS588, you have been hired to as chief architect to design a secure network for government agencies known as GovNet.The best cryptography experts at the NSA have recommended the following primitives:
- AES, a symmetric cipher. AES can be used securely with a 128-bit key and 128-bit block size. AES is efficient.
- RSA, a public-key cipher. RSA can be used securely with 2048-bit primes. RSA is slow.
- SHA, a cryptographic hash function. SHA produces a 160-bit digest.
- Tiny, a cryptographic pseudo-random number generator.
Consider the simple GovNet:
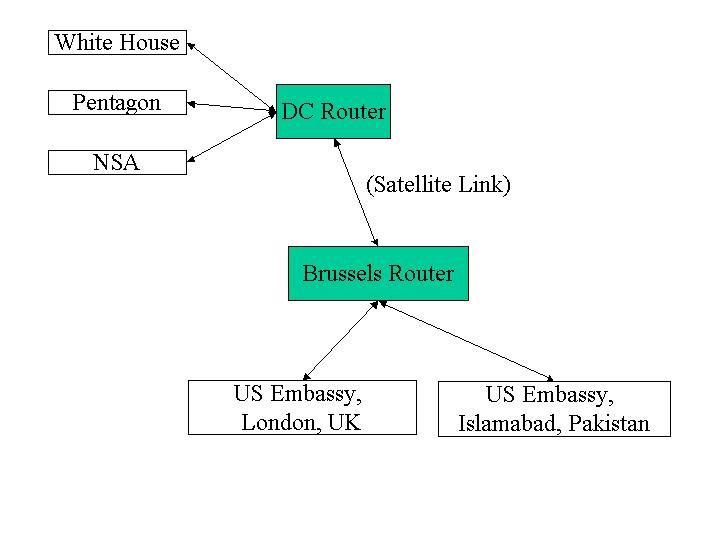
1. Router-Router Communication (25)
The NSA is worried about foreign governments tapping into the communication channels used by GovNet and recommends that all network transmissions be encrypted using AES (Rijndael). End users cannot be trusted to securely encrypt their transmissions, so encryption must be done by the routers before sending a message over a link.
Describe your design for sending messages between the DC and Brussels routers. It should explain clearly how a message is transmitted and received, how any keys are established and distributed, and any assumptions you make about performance and security tradeoffs. You may assume that the two routers are constructed in a secure facility in Langley, VA, and transported under close guard to secret locations in Washington, DC and Brussels, Belgium.
All satellite transmissions, of course, can be intercepted. The NSA reminds you that it would be unwise to transmit a large amount of data using the same key. The routers can store a few kilobytes of information.
Assume that the routers are kept in physically secure locations guarded by trustworthy soldiers, so there is no chance they could be compromised.
2. Joining the GovNet (25)
Agencies on the GovNet set up a gateway router that is connected over a land-line to one of the master routers. For example, the Pentagon sets up a gateway connected to the DC router. You may assume agencies join the GovNet infrequently, but need to do so with equipment they install locally. (That is, the gateway router that is installed at the Pentagon should not come preconfigured with any secrets stored on it, since it is vulnerable to tampering before it is installed in a secure location.)
Describe the process for an agency to set up a gateway router for the GovNet. Explain clearly how messages are transmitted between that gateway router and the master router. You should not assume the land-line connection between the two routers can be protected from passive or active eavesdropping.
3. Setting up Desktop Machines (25)
Once an agency has a gateway router, it should be able to set up local area network machines to be on the GovNet.
Penny Thrifty suggests that the GovNet machines in the Pentagon can use the same local area network as the normal machines (connected through a different gateway router to the Internet) in the Pentagon since the internal wiring in the Pentagon is very secure.
Design a scheme for setting up local GovNet machines and explain how they send and receive messages through the GovNet gateway. To be useful, it must be possible to have GovNet machines on desktops in offices that are somewhat insecure.
Explain any unreasonable risks associated with running the GovNet machines on the same local area network as the normal, Internet-connected machines. What restrictions would you place on how the local machines are used?
4. Should we build GovNet? (25)
Write an essay (no longer than 1 page) arguing for or against establishing a GovNet. Your essay should be substantially more techincal than either of the background articles above.
2000 Final
Question
In June, President Cliton signed the Electronic Signatures in Global and National Commerce Act into law. The Act adopted the general rule that an electronic signature has the same legal status in transactions involving interstate commerce as a traditional signature. The Act, however, did not specify any technology requirements on what is required to create and validate an electronic signature.With a magnetic card and his dog Buddy's name as a password, President Clinton e-signed a bill Friday that will make electronic signatures as real as those on paper.
FoxNews, 30 June 2000
You have been hired to design a national infrastructure for securely creating and validating electronic signatures.
1. Signing a Document (35)
Describe clearly and precisely your design for signing a document.
Signers should be able to sign a document using a moderately inexpensive device that attaches to a standard PC. That device may include a small display (but not large enough to show an entire document) and one or more input devices. You should not assume that any single device manufacturer can be completely trusted, but can assume the likelihood of more than one independent company conspiring is low.
Your description should explain where the keys are stored and how they are generated, what algorithms you use, and how information is transferred between the PC and the signing device.
The signer of a document should be able to have some degree of confidence that she knows what she is signing (or at least, if she is tricked into signing something different that she can prove she was tricked).
The owner of a signing device should have some degree of confidence that someone who sneaks into his home and has access to the signing device will not be able to easily forge signed documents.
2. Validating a Signature (15)
Describe clearly and precisely your design for validating a signature. After validating a signature, the recipient should have good confidence that the signer signed the document. An independent judge should be able to validate the signature and content of the document if there are any disputes.
3. Other Issues (25)
Discuss any other issues that you think are important for the success and security of your national signatures infrastructure.
4. Vulnerability Analysis (25)
Describe the vulnerabilities of your system. What are the most frightening attacks? What countermeasures (don't necessarily limit yourself to only technical countermeasures) should be adopted to limit the risks?
