Puzzle
As usual, I had my packet sniffer on during the visit to Microstrategy, and intercepted these two seemingly random but apparently interesting bit steams:
C1 = 010110000111101100001110111010000000011101100000001110110110010111110011011110010000011100000011101110000000111010100100010100000101000010011101110111111110011000101101010000001001100111000110000011010100001110010110011011101011111101100000100101110110100000001101101100111011001001011010011101111101000100011000110110001100010011010010100011101010000100101010010101001100010110000100000000011000101101111110100101001010001100110101100111010110011110010000001011111000111101001100101010111110111101111001011010101111100100000101101010100001100001110001100100110110001001101100011100101101100111111111001111000100001111011010110101101111100111000000001100100110010010010010011101110011101010001000000011101000100111101000110011110101101000101000101011100110110011101101001011010100000000101101011101100101110111011000111010110011100000110101000111001100101000011010100010001000110111011010101100101111110101001010111100010110100000101111010110000001000011000101011011001010100010010111110000010110001011100010111011010011100011100101111001011001011000001001110111000011010000000110010100011110111111111001110010111111110011110000001110000000101101010011011000001000111001111110110011000111010101100010111110110000101111111111111011011000100000100111101111111111111111100100011110010111111011010000000110101100110011110000010101100011110101000010101000101000001011010100101001111001111111010110101101111011011010010000001000011101001111110000000001000111011010010110101101110101101000011110011001100010000101000001001000011101100110010010000100000001000101110011010110101000001100011001011011011000111100001010101110000011111000101000010100101100100011010111110001001000011001111001001100110101011001100000010010111000110111111001011101100010100000111000011010001101000010101001110100000101001100011101101101
C2 = 010000000100100100000100110000001010111110100111011010101110111000111001011100101111111101000101100110010101101000100000011001000111000000111101110110011110010100101111010111011011110100010110100011010100001111010110011100111010001101100000100101110110100000001101101100111011001001011010011101111101000100011000110110001100010011010010100011101010000100101010010101001100010110000100000000011000101100000010110001001100001010100110010101101110000000111001011110100100001100001100111110001010000101100100011101111100000110100000111110101001101100111010000111100110001001111100000000111010000101011110000111101111110010111100000011111010001011010111111001000000110010010011011000110001111000001001000111001010101001001110011001010101100001000010110101110010010101101101001011010000010010000101011001000111010100010010100011000001111110100001000111001001001000101011111010101001111000010101111100000111010101011010110011011111100101001101100110100000011100111001001111100101010100010101110100110010001010101101110001100011010001100100100101101101011010000001010000011010101000110000001010010010111111011101010010110110011111100100011011001110101100011010100000110100000010111010010101000100100101110010010000111110111110110010111101001000101100000011101101100101011101010100111101100111100011010010001111000110110111110001110001101101010011001010101001101011000001000100000111111010101011101110101110011011011110010100111010001101100110010101011000100111001000110010111110011100101010011110111100110000010111001110101010011001110111011110101010100101101100010001110011110010100101000001011011001101111011101111110111011110100100010100001111101100000011001110011100101100100111111110101011010100001000101001010100100010100110011110101101010111100100100010010001000101101101011101001011100001011001011011011001
Although each message would be perfectly secure by itself (assuming a perfectly random key was used), you may be able to figure out their contents using the same technique John Tiltman used to determine the key used from the two intercepted messages.
You may find this Python code helpful for doing bit manipulations.
Note added 27 October: The encrypted messages unforuntately have a
long overlapping part where both messages are identical! This makes
it so that you don't actually have a two-time pad for that segment,
but a one-time pad, which is unbreakable (other than any possible
weaknesses in Python's Crypto.Random which I used to generate the
key). The text that is identical in the two messages is into this
crypto stuff. Sorry for the touble this caused to anyone who tried
to break the impossible part of the puzzle! Congratulations to
Gabriel Espinola Ibarra for essentially solving it (other than the
impossible part).
Annotated Slides
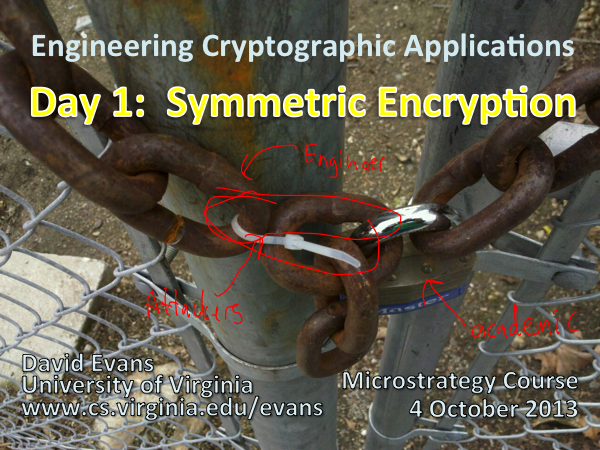 |
Academics focus on the shiny, complicated parts. Attackers go after the flimsy, plastic parts. Engineers should focus mostly on using the rusty, solid, well-understood parts and avoiding introducing flimsy, plastic parts. |
 |
|
 |
|
 |
|
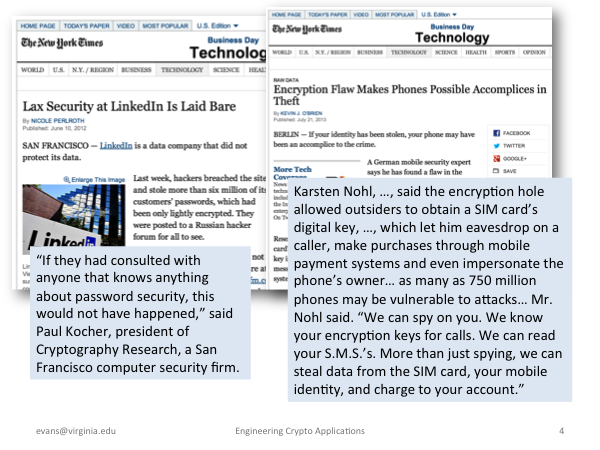 |
Lax Security at LinkedIn Is Laid Bare, New York Times, 10 June 2012 (you will understand enough to not make these kinds of mistakes by the second sesson) Encryption Flaw Makes Phones Possible Accomplices in Theft, New York Times, 21 July 2013. (this was partly a result of implementing systems today using legacy technologies that are not nearly strong enough to thwart low-resource attacks today) |
 |
Next: Kerckhoffs' Principle
Jefferson's Wheel
Cryptanalysis
Modern Symmetric Ciphers